The Cyber Monitoring Centre (CMC), in its first live public assessment of the financial impact on the UK of a cyber incident, categorises the disruption of retailers M&S and Co-op as a Category 2 systemic event. The CMC estimates the total financial impact across affected parties at £270 million to £440 million.
In April 2025, UK retailers Marks & Spencer (M&S) and Co-op were both affected by a cyber ransomware incident that resulted in disruption to critical business functions, and in which customer data was exfiltrated1
The Cyber Monitoring Centre (CMC) has analysed the event in line with its mission to categorise systemic cyber incidents in the UK and provide independent, considered analysis that can be used to increase the UK’s cyber resilience.
Given that one threat actor claimed responsibility for both M&S and Co-op, the close timing, and the similar tactics, techniques, and procedures (TTPs), CMC has assessed the incidents as a single combined cyber event. It has not included an incident affecting UK retailer Harrods at a similar time, or other retailers also reported to have been impacted in April and May, given the low level of information about the cause and impact.
The CMC’s assessment includes an estimate of the financial impact of the event, insights into its implications, and recommendations for future preparedness, to improve cyber mitigation and response plans. The CMC’s assessment and recommendations draw on data collected on the event’s impact, coupled with input from subject matter experts and the collective experience and expertise of its Technical Committee, chaired by Ciaran Martin. The CMC is constantly looking to improve its methodology and data, and is willing to discuss its findings – confidentially – with any party with value to add to the assessment.
Event Overview and Categorisation
The CMC has classified this incident as a Category 2 systemic event based on the categorisation matrix as defined in our methodology. This reflects its substantial financial impact and the economic reverberations across third-party suppliers, franchisees, and supporting services.
The Cyber Monitoring Matrix Showing the Positioning of this Event
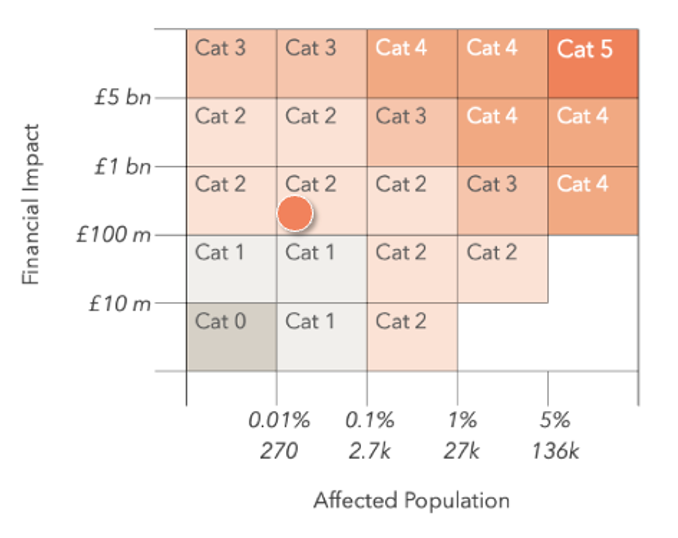
The impact from this event is “narrow and deep”, having significant implications for two companies, and knock-on effects for suppliers, partners, and service providers. This contrasts with a “shallow and broad” event like last year’s CrowdStrike event, where a large number of businesses across the economy were affected but the impact to any one company was far smaller. We are yet to see a deep and broad category 4 or category 5 event impact the UK. Had there been further widespread disruption in the sector, the categorisation could have been higher, but because the impact was confined to two companies and their partners, it is judged to be at the lower end of severity on the CMC’s scale.
Although both of the targeted companies suffered business disruption, data loss, and costs for incident response and IT rebuild, business disruption drives the vast majority of the financial cost. Most of the estimated disruption cost is faced by the two companies, but our analysis seeks to estimate the wider cost to partners, suppliers and others.
Attribution is ongoing, but current indicators suggest the same threat actor targeted M&S and Co-op using similar TTPs. The initial access vector is believed to involve social engineering, with reports suggesting compromised credentials and potential abuse of IT helpdesk processes.
Estimated Financial Impact
Using available data and established modelling, the CMC estimates the total financial impact of the event across affected parties at £270 million – £440 million. This includes:
- Direct business interruption costs resulting from lost sales (the bulk of the cost) for M&S, Co-op, franchisees, and suppliers
- Incident response and IT restoration costs for M&S and Co-op
- Legal and notification costs for M&S and Co-op
M&S described in its full-year results published on 21 May an expected impact of the incident of “c.£300m for 2025/26, which will be reduced through management of costs, insurance and trading actions”2 The CMC’s assessment is independent of, although broadly consistent with, this estimate.
Based on the M&S financial statement and comments made in late May, we originally anticipated an early July return of online shopping. The return of limited online sales (approximately a third of online fashion items and no home and beauty products initially available) a month ahead of these assumptions, reduced our overall estimate of the financial impact. Our model indicated that the financial impact of having no online sales was a loss to the business of just over £1.3M per day – this is less than the total loss in turnover as it takes into account reductions in orders, stock that can be resold later, and not having to pay other variable costs.
The CMC’s estimates are based on public and commercial data sources including Fable Data, which provided a representative sample of transaction-level consumer spending at M&S and Co-op. We have not included any ransom payments as there is no evidence at this point that a ransom was paid or not paid.
Key Insights from the CMC Analysis
- Consumer sales impact (M&S): For M&S, Fable data shows a reduction in average daily spend of 22% during the event for the period online shopping was unavailable, with online sales dropping to near zero and in-store sales down almost 15%. Early media reports focused on the failure of contactless payment methods, but the true impact was significantly broader and driven primarily by the prolonged disruption to online sales and in-store stock shortages.
- Consumer sales impact (Co-op): For Co-op, Fable data shows an average fall in daily spend of 11% in the first 30 days of the event.
- Supplier exposure: M&S’s distinct own-label model and exclusive contracts mean that it is harder for suppliers to re-route goods, particularly where packaging or safety regulations apply (e.g. M&S prepared foods and meat). Some suppliers expressed concern about cash flow, though M&S has been described as proactive in supporting partners.
- Concentration risk in more remote areas: In remote and rural areas (e.g. the Highlands and Islands in Scotland), Co-op acts as a sole provider. Service disruption in these regions illustrates the broader societal impact cyber events can trigger through concentrated retail supply chains. Co-op are said to have prioritised supplying these stores.
- Retail operational fragility: The event underscores retail sector vulnerabilities tied to just-in-time stock systems, lack of back-end storage, and high dependency on IT-driven order flows. When systems fail, it is challenging to revert to manual processes.
Challenges and Caveats
- The analysis is based on the available data and subject-matter expert discussions up to and including 10 June. We have made assumptions about how quickly M&S and Co-op will make a full recovery after this date.
- Assumptions were made about the relationship between loss of revenue (captured in the Fable data) and the financial loss to M&S and Co-op based on historical benchmarking and expert discussions. Both retailers publish high level financial information, but the detailed information that would be required to get a better understanding of the relationship between revenue and financial loss is not publicly disclosed. Given that business interruption is the primary driver of the loss, our model is sensitive to these assumptions.
- Incident response and IT restorations costs, and legal and notification costs were benchmarked based on historical events and discussions with the Technical Committee. Individual estimates for these costs have not been released by M&S or Co-op. Out of these additional costs, the most significant is the cost to rebuild IT systems.
Recommendations for Future Preparedness of the Retail Sector
The event illustrates the importance of:
- Stress-testing business continuity and crisis response plans for ransomware attacks, including fallback procedures for manual ordering and inventory control and the ability at least to partially restore key services as quickly as possible. Alongside the exercising and testing of technical and operational contingency processes and procedures, it is becoming increasingly important to test and validate crisis communications plans, to maintain confidence and trust across customers, suppliers, and, for listed organisations, shareholders.
- Ensuring financial stability and flexibility to survive large-scale operational disruption. Costs from business interruption – and the costs of IT recovery – can quickly mount up and retailers, like all businesses, should run stress tests and make sure they have capital available or adequate insurance protection to enable recovery.
- Improving cyber hygiene across service providers and the IT services supply chain, particularly IT support desks and third-party vendors. Retailers should test whether they understand their dependencies, and whether they can quantify their risks.
- The paramount importance of access and identity management. Assuming reports of the nature of the breaches are accurate, it demonstrates that internal privilege escalation controls are vital to reduce exposure to social engineering-based attacks.
The CMC’s analysis aims to provide transparency and support coordinated improvements in cyber resilience. This event shows how even a contained cyber attack can ripple across sectors and geographies, affecting businesses, customers, and critical supply networks.
We will continue to work with industry, insurers, and government to learn from this event and help reduce the impact of future systemic cyber threats.
About the Cyber Monitoring Centre
The Cyber Monitoring Centre is an independent, non-profit organisation responsible for analysing and categorising cyber events that impact UK organisations.
Events are categorised by an independent technical committee made up of leading cyber experts and based on analyses of data from leading providers. Event categorisation and event reports are provided free of charge to any interested organisations and individuals to help increase the understanding of the impact of cyber events and improve cyber mitigation and response plans.
Full details of the CMC’s methodology and categorisation matrix can be found here and full details of the CMC’s Technical Committee can be found here.
Disclaimer
The Cyber Monitoring Centre provides event categorisations free of charge that are publicly available to all. No liability is accepted for the use of, or reliance on event categories. Event categorisations are determined based on the information available up to the date of the Technical Committee meeting. All reasonable endeavours are used to try to ensure accuracy of the information used in providing the event categorisation. However, the Cyber Monitoring Centre makes no representations or warranties of any kind, whether express or implied, as to the completeness, accuracy, reliability or suitability of the event categorisation or any supporting information, any of which may be subject to change without notice. The Cyber Monitoring Centre doesn’t release precise loss estimates, providing instead the loss estimate range.
1 https://corporate.marksandspencer.com/cyber-update
https://www.co-operative.coop/media/news-releases/cyber-incident-update
2 https://corporate.marksandspencer.com/sites/marksandspencer/files/05-2025/fy25-rns.pdf